Android Developers Blog: Upgrading Android Attestation: Remote Provisioning
Posted by Max Bires, Software program Engineer
Attestation as a characteristic has been mandated since Android 8.0. As releases have come and gone, it has more and more grow to be increasingly more central to belief for quite a lot of options and companies reminiscent of SafetyNet, Id Credential, Digital Automobile Key, and quite a lot of third occasion libraries. In gentle of this, it’s time we revisited our attestation infrastructure to tighten up the safety of our belief chain and enhance the recoverability of gadget belief within the occasion of recognized vulnerabilities.
Beginning in Android 12.0, we can be offering an possibility to switch in-factory non-public key provisioning with a mix of in-factory public key extraction and over-the-air certificates provisioning with short-lived certificates. This scheme can be mandated in Android 13.0. We name this new scheme Distant Key Provisioning.
Who This Impacts?
OEMs/ODMs
Gadget producers will not be provisioning attestation non-public keys on to gadgets within the manufacturing unit, eradicating the burden of getting to handle secrets and techniques within the manufacturing unit for attestation.
Relying Events, Probably
Described additional down beneath, the format, algorithms, and size of the certificates chain in an attestation can be altering. If a relying occasion has arrange their certificates validation code to very strictly match the legacy certificates chain construction, then this code will must be up to date.
Why Change?
The 2 major motivating components for altering the way in which we provision attestation certificates to gadgets are to permit gadgets to be recovered post-compromise and to tighten up the attestation provide chain. In right this moment’s attestation scheme, if a tool mannequin is discovered to be compromised in a means that impacts the belief sign of an attestation, or if a secret’s leaked by way of some mechanism, the important thing have to be revoked. Because of the growing variety of companies that depend on the attestation key sign, this will have a big influence on the buyer whose gadget is affected.
This modification permits us to cease provisioning to gadgets which are on known-compromised software program, and take away the potential for unintentional key leakage. This can go a good distance in decreasing the potential for service disruption to the person.
How Does This Work?
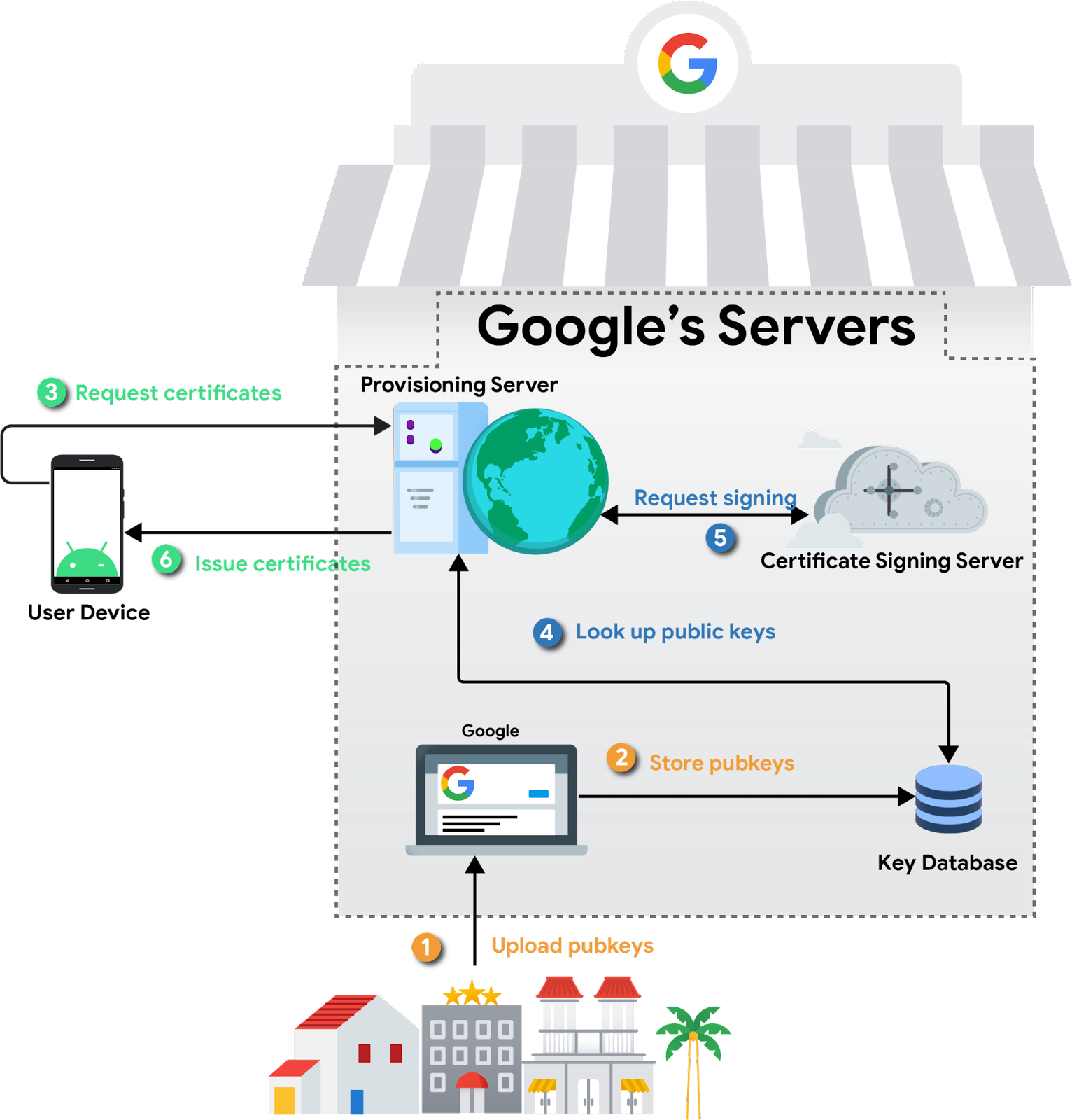
A novel, static keypair is generated by every gadget, and the general public portion of this keypair is extracted by the OEM of their manufacturing unit. These public keys are then uploaded to Google servers, the place they function the idea of belief for provisioning later. The non-public key by no means leaves the safe setting by which it’s generated.
When a tool is unboxed and related to the web, it would generate a certificates signing request for keys it has generated, signing it with the non-public key that corresponds to the general public key collected within the manufacturing unit. Backend servers will confirm the authenticity of the request after which signal the general public keys, returning the certificates chains. Keystore will then retailer these certificates chains, assigning them to apps every time an attestation is requested.
This circulate will occur recurrently upon expiration of the certificates or exhaustion of the present key provide. The scheme is privateness preserving in that every utility receives a distinct attestation key, and the keys themselves are rotated recurrently. Moreover, Google backend servers are segmented such that the server which verifies the gadget’s public key doesn’t see the connected attestation keys. This implies it isn’t doable for Google to correlate attestation keys again to a specific gadget that requested them.
What’s Altering from a Technical Standpoint?
Finish customers gained’t discover any adjustments. Builders that leverage attestation will need to be careful for the next adjustments:
- Certificates Chain Construction
- Because of the nature of our new on-line provisioning infrastructure, the chain size is longer than it was beforehand, and is topic to alter.
- Root of Belief
- The foundation of belief will finally be up to date from the present RSA key to an ECDSA key.
- RSA Attestation Deprecation
- All keys generated and attested by KeyMint can be signed with an ECDSA key and corresponding certificates chain. Beforehand, uneven keys had been signed by their corresponding algorithm.
- Brief-Lived Certificates and Attestation Keys
- Certificates provisioned to gadgets will typically be legitimate for as much as two months earlier than they expire and are rotated.
Take a comment